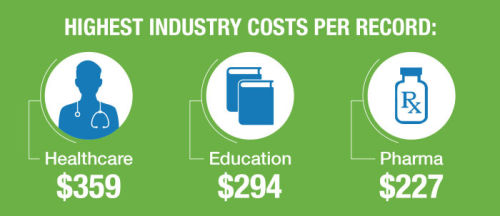
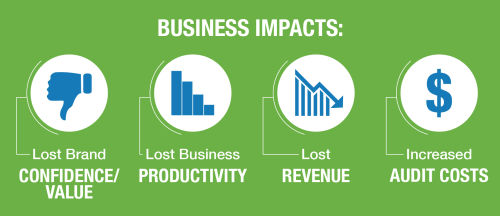
We Locate IT Security Vulnerabilities
In today’s highly connected and integrated world of business, security is a main concern. From government entities to major retailers to healthcare providers, many have been victims of data breach. Our comprehensive Security Assessment identifies vulnerabilities in your system to comply with HIPAA requirements. Our HIPAA audit focuses on assessing what safeguards your system has already, identifying what policies or documentation are missing, and recommending solutions to resolve issues.
Request a Inquiry
ALIS IT Security Audit focuses on:
- Physical safeguards
- Technical safeguards
- Disaster recovery and data backup plan
- Network security
- Computer usage
- Review security policies
- Password policies
- Secure email and encryption
- Logging and monitoring
- PCI compliance
- Penetration testing
- Logging and auditing
- Detailed documentation
- Identify gaps
- Recommend solutions
- Assist in implementing solutions
- Identify software with PHI
- Identify BA’s
- Review IT policies
- Email phishing
- Breach notification policy